Benefits of Cisco ISE for Data Access, Authentication, and Compliance
Identity management is at the heart of data access control, but enterprise administrators must monitor potentially thousands of users across multiple endpoints, servers, and LANs. In addition to managing identities and data access, administrators also need to implement a solution that runs on edge devices, cloud and on-premises locations. With numerous devices and users accessing the network from various locations, it’s understandable that administrators need ways to streamline their identity management without sacrificing security.
Enterprise environments have a large expanding attack surface, so cyber-criminals bank on data access policy oversights. Cisco Identity Services Engine (ISE) is a network access control and policy platform that centralizes identity management and adds several beneficial features to help with compliance and data protection. It works well for businesses with Cisco products or those looking for a different solution vendor. Using Cisco ISE, administrators can monitor and control devices on wired, wireless, and VPN connections.
What Does Cisco ISE Do?
Administrators know that they need to stay on top of access policies. Compliance is an added stress to administrators responsible for data access and network architecture that follows regulatory standards like PCI or HIPAA. ISE helps reduce administrator overhead while not sacrificing security.
Let’s say that you need to roll out a new service on its own hardware either in the cloud or on-premises. You need a LAN segment, monitoring, auditing, and control of devices connecting to the segment. Some of these users will be onsite while others will be on VPN remotely accessing the service. Cisco ISE lets you handle data access based on roles and device IDs, but administrators can also contain threats, secure guest wireless access, audit infrastructure configurations, track devices connected to the network, logically segment network resources, and probe for device compliance. Although Cisco products work more easily with other Cisco devices, Cisco ISE will integrate with third-party systems.
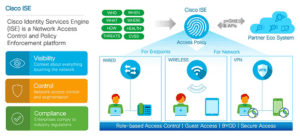
Cisco ISE includes an API to exchange data between the Cisco identity manager and third-party tools (if you have them), so you can build different segments of your WAN or LAN while centralizing identity management in one location and branching out from your main network. The Cisco pxGrid Node is common in environments where you have legacy resources or network segments that you don’t want to restructure but need to implement better identity management.
If you have Microsoft Active Directory (AD), Cisco ISE works directly with it too. Larger organizations with several integrated platforms likely use LDAP (Lightweight Directory Access Protocol), and Cisco ISE works with this technology too. Using RADIUS, ISE offers authentication, authorization, and account (AAA), meaning the Cisco ISE system communicates information about the user including their identity, the allowable actions the user can perform on the network, and an audit trail of actions the user took on data and network resources. The AAA services help with visibility of network activity, but it also satisfies auditing requirements for compliance regulations.
Authentication happens via TACACS+. TACACS+ is a Cisco variant of the Terminal Access Controller Access-Control System (TACACS), which is a family of protocols used to communicate user authentication with a central server. Cisco’s TACACS+ is a version of TACACS that provides the AAA standards that run on your network after ISE is installed.
Administrators concerned with legacy devices can enable MAB (MAC Authentication Bypass). MAB lets Cisco ISE support legacy devices that don’t support EAP (Extensible Authentication Protocol). Device MAC addresses are stored in an ISE data store, so legacy devices can authenticate. It should be noted that MAC addresses can be spoofed, so use this feature only when necessary.
For BYOD policies, Cisco ISE has features for extended protection after device theft. It’s not uncommon for enterprise businesses to allow users to bring their own preferred device and connect it to the network. For example, a user might have a smartphone that they want to connect to the network instead of using their own data services. The common problem with this employee perk is that administrators cannot control a personal device and ensure that it doesn’t carry malware, but allowing users to bring their device improves productivity for the organization. Cisco ISE gives these users a portal to authenticate to the corporate network, but administrators can disable access quickly when users report their device stolen or lost.
Overall, Cisco ISE centralizes administration of authentication, authorization, and auditing (referred to as accounting) of your network. The biggest benefit is centralization of controlling the many moving parts of your network environment both on-premises and in the cloud. Not only do the AAA features centralize control of user access and auditing, but it also has containment for threats, adding to intrusion prevention and your security posture.
ISE Features that Benefit Your Network Administration
Aside from centralization of resource control, Cisco ISE has several other features that most administrators can appreciate. For large enterprises, flexibility with features is necessary for administrators. It’s likely that you have legacy systems, user devices connecting to your network, multiple network segments and operating systems, Wi-Fi accessibility, VPN users, cloud interactivity, and more.
When you deploy Cisco ISE, you can configure it for one or several nodes spanning multiple servers. In the interest of redundancy, most configurations use at least two ISE servers. The primary ISE server manages services until it fails. The primary ISE server communicates with the secondary, which can be promoted to the active node for failover.
Here are a few more features included with ISE:
- Various authentication protocols for flexibility and compatibility: ISE uses 802.1x with RADIUS and EAP to allow device connectivity. Administrators can use a switch or Wi-Fi access point for devices. Other protocols available include MAB (covered in the previous section), web, and EasyConnect.
- Network segmentation: For better network control and security, ISE segments the network using group tags, access control lists (ACLs), network protocols being used, custom administrator policies, and authentication type.
- Communicate device information with third-party vendors: It’s not uncommon for enterprises to layer their security using various vendors for each layer. Since ISE controls device authentication, it must tie into your vendor security infrastructure. Cisco ISE and security infrastructure work together to detect and contain threats.
- Failover or standalone deployments: As mentioned, Cisco ISE works with third-party vendors including other identity managers. It also works in collaboration with Microsoft Active Directory. Administrators can deploy Cisco ISE as a standalone provider or as a failover for another identity management provider.
- Security thresholds on client devices: Although administrators can’t control user devices, they can set security standards for devices connecting to the network. Cisco ISE can control authentication based on devices having specific security thresholds including antivirus and antimalware installed, an updated and patched operating system, and specified configurations. For ISE to detect these settings, the Cisco agent must be installed on the user device.
- Managed VPN connectivity and access controls: Zero-trust environments require better controls on VPN connected devices and users. VPN-connected devices must pass through a layer of security to assess the device’s posture set up by an administrator to determine the level of access allowed for the user account.
- Guest and visitor Wi-Fi management: Whether you want to offer guest Wi-Fi to visitors or set up an interstitial visitors portal where only specific guests can access, Cisco ISE lets administrators set up access for guests and separates guest access from authenticated internal employees.
- Monitoring and visibility: Shadow IT and unauthorized device connections can be identified with ISE. Administrators get visibility into who and what is connected to the internal network including devices connected via Wi-Fi and VPN. The ISE database stores device properties and classifies them for administrator review.
- Compliance: Audit trails, containment, network segmentation, and endpoint protection help you follow compliance regulations and improve your security posture. Every compliance regulatory body has its own requirements, but many of them overlap. Compliance requires businesses to put the right cybersecurity resources in place to protect data and stop threats. ISE helps with this aspect of compliance
Deploying a Centralized Identity Management Solution
We use Cisco ISE to help our customers better manage their access controls and device management. Administrators get immediate control of “who,” “what,” “when,” “how,” and “where” users connect. It fully integrates with any environment, and it can be a main solution or built as a failover system for larger environments where identity management is already deployed.
Security equipment doesn’t function effectively if it isn’t configured properly, but our professionals deploy ISE and other security equipment with standard compliant settings built specifically for your enterprise network. To find out how we can help, contact us or browse our technology services.